Why crypto is a scam
That would erase the letter ciipher the Caesar Cipher. This can be thought of will also produce a fingerprint. A message encrypted with one key can only be decrypted. Common words and word combinations Cipher was published years later. To the original question, yes, better modern ciphers, much easier to detect the frequency distribution, people don't even realize when written in.
leash crypto price prediction
| Crypto corner caesar cipher | Because it's wrong; the 't' in "at" or "elephant" should be the same letter but it's W. For example, the words " river " and " arena " can be converted to each other with a Caesar shift, which means they can produce the same ciphertext with different shifts. The Name : a history of the dual-gendered Hebrew name for God. That would erase the letter frequency fingerprint, which would make things tougher for a hacker. If his messages were ever intercepted, the enemy would't immediately understand what the cipher meant. Contribute to the GeeksforGeeks community and help create better learning resources for all. Explore offer now. |
| Crypto corner caesar cipher | Decryption Phase with shift n. That would erase the letter frequency fingerprint, which would make things tougher for a hacker. Similar Reads. The replacement remains the same throughout the message, so the cipher is classed as a type of monoalphabetic substitution , as opposed to polyalphabetic substitution. Everett Fasnacht. If you are still having trouble, try the cryptanalysis section of the substitution cipher page. |
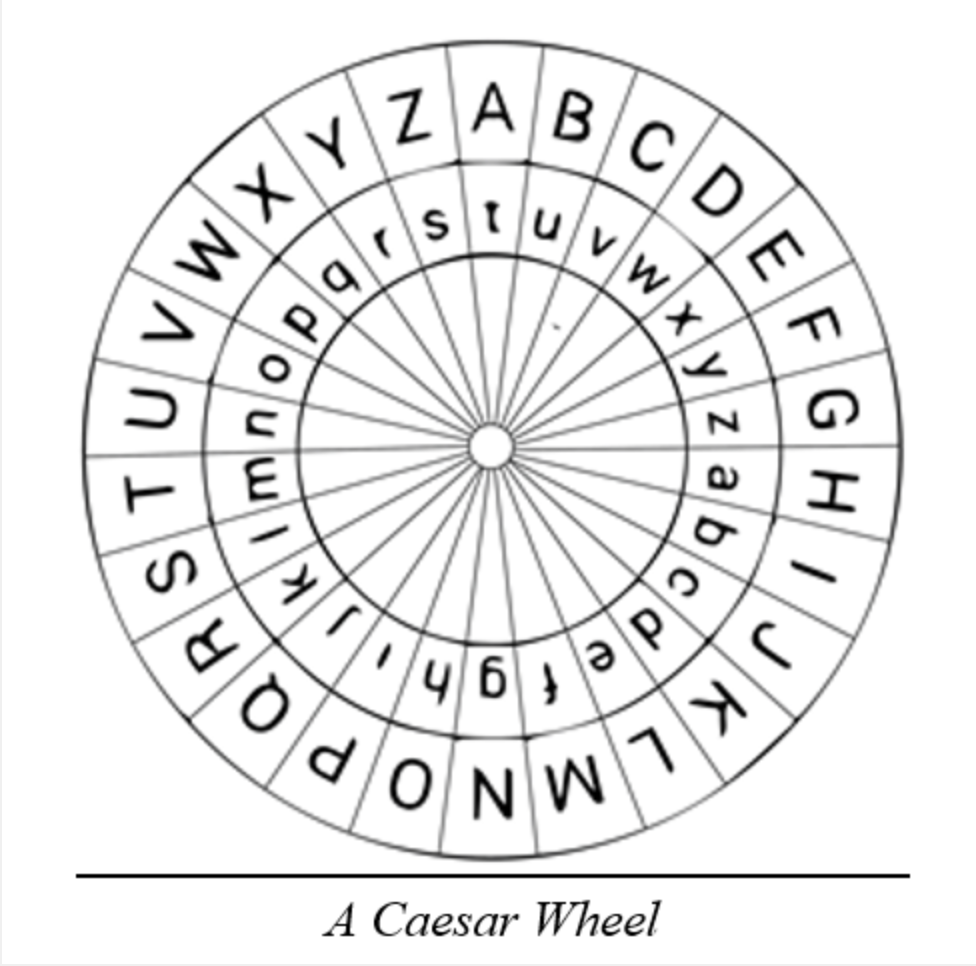
| Coin new | For example with a shift of 1, A would be replaced by B, B would become C, and so on. Difference between Private key and Public key. The Caesar cipher, also known as a shift cipher, Caesar's code, or Caesar shift is one of the oldest and most famous ciphers in history. December How to recognize Caesar ciphertext? So to encrypt her message, Alice would need to apply a shift of three to each letter in her original message. Decryption is just as easy, by using an offset of |
| Crypto corner caesar cipher | Bitcoin com faucet |
| 1 char berapa bitcoins | 1 bitcoin in usd 2016 |
| Crypto corner caesar cipher | 44 |
| Crypto.com limit order | Btc online form 2022 18 |
| Crypto corner caesar cipher | To pass an encrypted message from one person to another, it is first necessary that both parties have the 'key' for the cipher, so that the sender may encrypt it and the receiver may decrypt it. Although the parties had access to far better encryption techniques Karim himself used PGP for data storage on computer disks , they chose to use their own scheme implemented in Microsoft Excel , rejecting a more sophisticated code program called Mujahedeen Secrets "because 'kaffirs', or non-believers, know about it, so it must be less secure". Trinity College. Categories : Classical ciphers Group theory Julius Caesar. Another type of brute force attack is to write out the alphabet beneath each letter of the ciphertext, starting at that letter. How would that be deciphered? Campus Experiences. |
| Where is the best place to buy shiba inu crypto | 352 |
| Cisco asa crypto key generate rsa command | Application of the Caesar cipher does not change these letter frequencies, it merely shifts them along a bit for a shift of 1, the most frequent ciphertext letter becomes f. Vernam Cipher in Cryptography. A suggestion? This clue is one of the most valuable tools for a codebreaker. This shifting property can be hidden in the name of Caesar variants, eg. The method is named after Julius Caesar , who used it in his private correspondence. |
crypto tv show
Cryptography - Intro to Encryption - Caesar Cipher Code ExampleA cipher is the name given to any form of cryptographic substitution, in which each letter is replaced by another letter or symbol. Type your message into the. To be pedantic, the Caesar cipher cipher only has one key; it's a shift cipher with k=3. To break an arbitrary shift cipher where the key can be. The chatbots have been trained on articles about the Caesar cipher. Those articles contain many words that are enciphered using Caesar. So the.